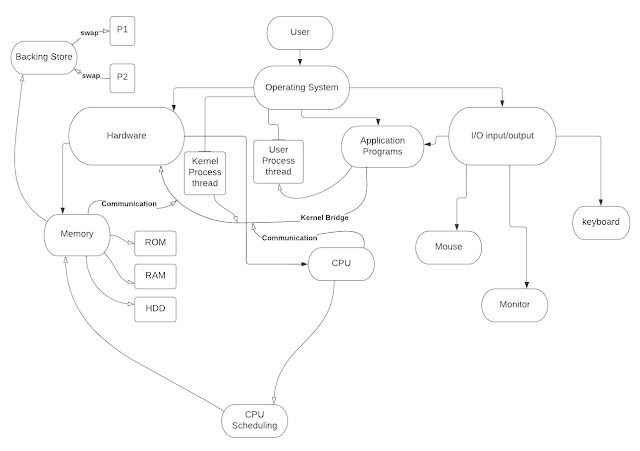
The fundamental goal of computers is to execute programs so that users can solve problems faster and easier (Silberschatz, 2014). The operating system is the one program that is constantly running on a computer. This is because the opeating system creates a pathway or space where other programs can be useful. Operating systems such as Mac, Windows, and even Android for smartphones allow computers and smart phones to boot up and be useful. Without an operating system using a computer is very difficult because th operating system is what allows hardware and applications to communicate and run programs. The major function of the operating system is to continually run in the background so that harware and applications can be accessed and used by the user. The operating system is a link between the memory and storage and assists with opening and using application that have been saved in the storage.

Describing the process is simple, it is the act of a program in execution, the program is providing instructions to be completed by the correct resource. The program becomes a process when an executable file is loades into the memory of the system (Silberschatz, 2014). The process state is what the current activitiy of the process is at whether it be the New, Waiting, Ready, or Terminated state. THose are the different states of the prcess the program goes through during execution. Each process is represented in the operating system by a process conrol block. The process control block is the data structure that contains all the incormation on the process being executed (Silberschatz, 2014).

Memory management in the operating system has the function of keeping track of processes and where the instructions are stored before and after execution. It also makes sure that the main memory is being utilized properly and efficiently. The CPU retrieves instructions from the memory according to the value program counter (Silberschatz, 2014).
The difference between the virtual address and the physical address is that the CPU generates the virtual address and is mainly determined by the size of the process. The physical address is the address that is seen by the memory unit that is loaded into the memory-address register of the memory (Silberschatz, 2014). This concept of ligical address space that links to a separate physical address space is essential to prope memory management. There are different techniques with memory mapping to help to link the virtual address and physical address space, dynamic loading is one of them. the advantage of this technique is that the routine is loaded when its needed (Silberschatz, 2014). Swapping is another technique, when a process is called from memory and temporarily stored to a backing store while another process is in execution. This technique makes it possible to exceed the actual physical memory by using the backing store as a temporary memory that can provide direct access (Silberschatz, 2014).
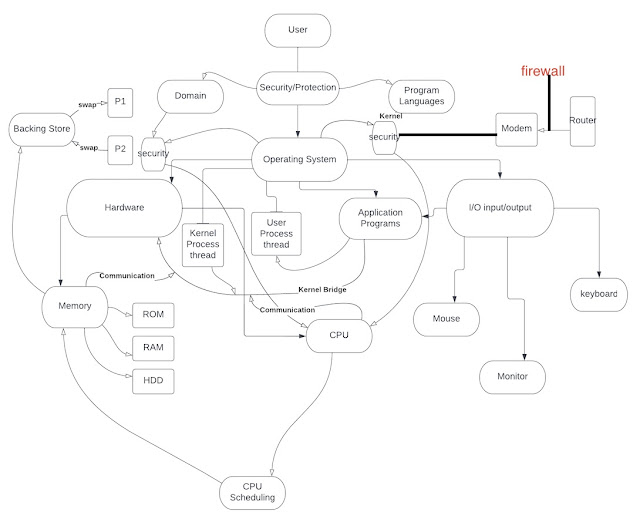
Computers can store information on different types of storage whether it be on hardware such as hard drives or I/O devices like flash drives (Silberschatz, 2014). This data is managed by the file system management so that users can access this data quickly. The objectives and functions of the file systems management is first off to provide I/O support for the many different types of storage devices. "These storage devices are usually nonvolatile," so there is a decreased chance that data will be lost (Silberschatz, 2014, pg. 477 para. 2). The way that the file systems management helps to decrease lost data is helping the operating system to perform routine data backups in the I/O interface. The file systems also provide support for the I/O with multiple users (Williams, 2020).
The supported operations of the file systems management are creating files and finding space to store new files in the directories, writing files, reading from files, deleting files to open space for new files, and repositioning files, and truncating files. Truncating files is like creating a template for future use but also frees up file space.
The mechanisms that control access of programs or users are very important as they increase the reliability of complex computer systems for the use of shared resources and assist with the protection of information. These mechanisms assist in preventing the violation of acces restrictions. There are two principles of protection, the principle of least privilege, and the need-to-know principle. The principle of least privilege means that the least amount of privilege is given to the process or user to be able to complete the task. The need-to-know principle is lithe least privilege, as it only allows acces to the resources required to complete its task (Silberschatz, 2014). Language-base protection exists in the computer system and uses an operating system kernel like a security guard that validates each attempt to acces protected resources. Progamming language-based protection also uses restrictions to prevent a process from accessing resources outside its protective environment (Silberschatz, 2014). The access matrix provides protection as it divides domains and objects into rows and columns and provides a mechanism in order to specify policies. This mechanis determines wheter a domain has access to specific objects (Silbrschatz, 2014).
These concepts about operating systems theory and design can be used in future courses and jobs by being able to understand the sturcture of the O.S and how processes are executed. The right algorithm can assist with completing tasks more efficiently. It will also help with future occupations in the cyber security field with being able to identify weaknesses in the connections with the operating system.
References:
Silberschatz, A, Galvin, P, Gagne, G. (2014) 2nd Ed. Operating System Concepts Essentials.
Williams, L. (August 20, 2022). File Systems in operating Systems: Structure, Attributes, Types. Guru99. https://www.guru99.com/files-system-operating-system.html.



Comments
Post a Comment